auth parameter in the createBlock function within your block definition, as well as in all createAction functions within your action definitions.
Each block can use only one authentication type.
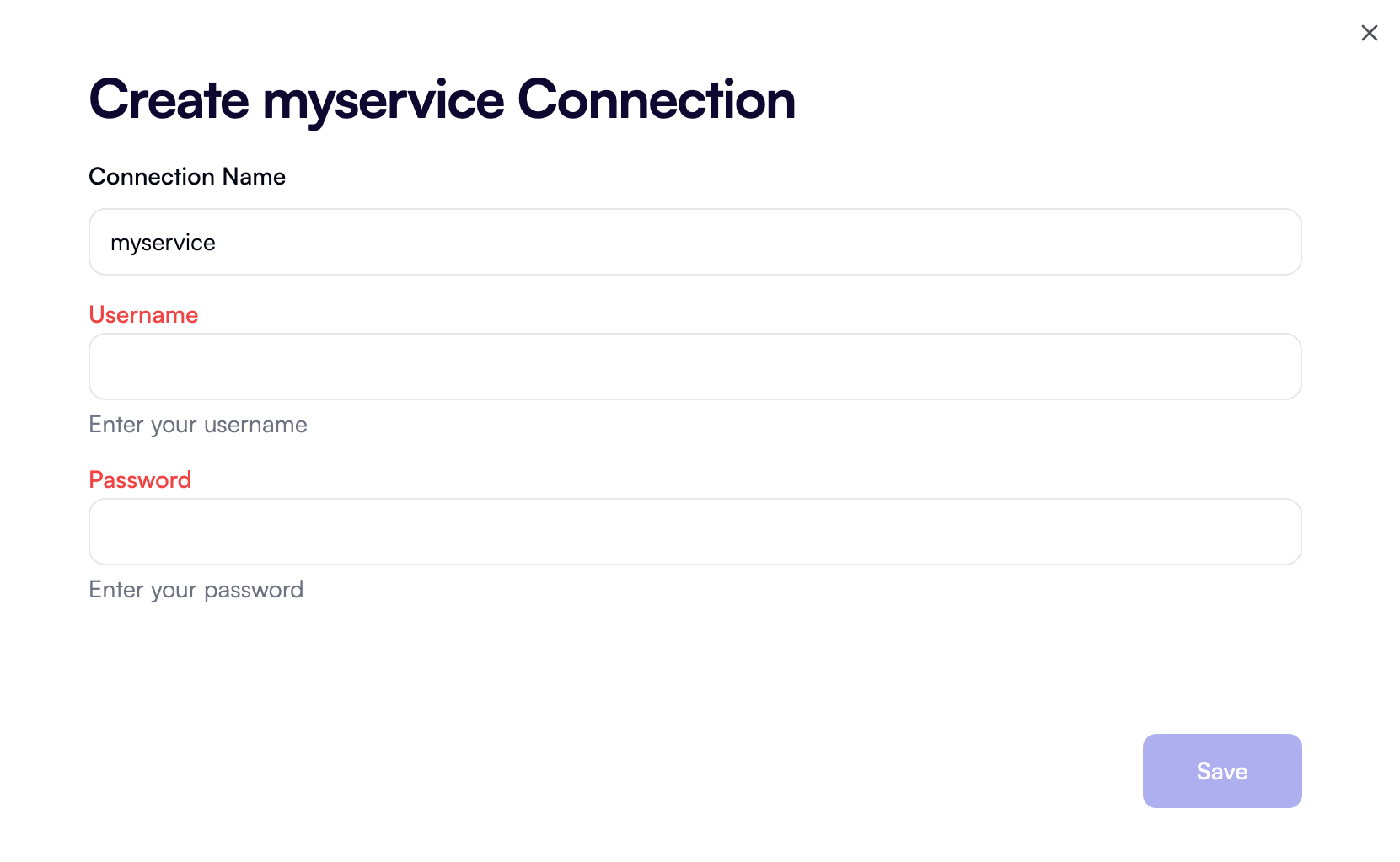
Basic authentication
This authentication type collects a username and password as two separate fields. It can also be used to pass an API key and an API secret, or similar pairs of public/private credentials, in which case they are sent in the HTTPAuthorization: Basic header.
Secret-based authentication
Use secret-based authentication when an API key is all that’s required to authenticate with a service you’re integrating with, and the service’s base URL is always the same. This authentication type is used by many OpenOps blocks, including CloudHealth, CloudZero, Flexera, Linear, Monday.com, nOps, and Vantage.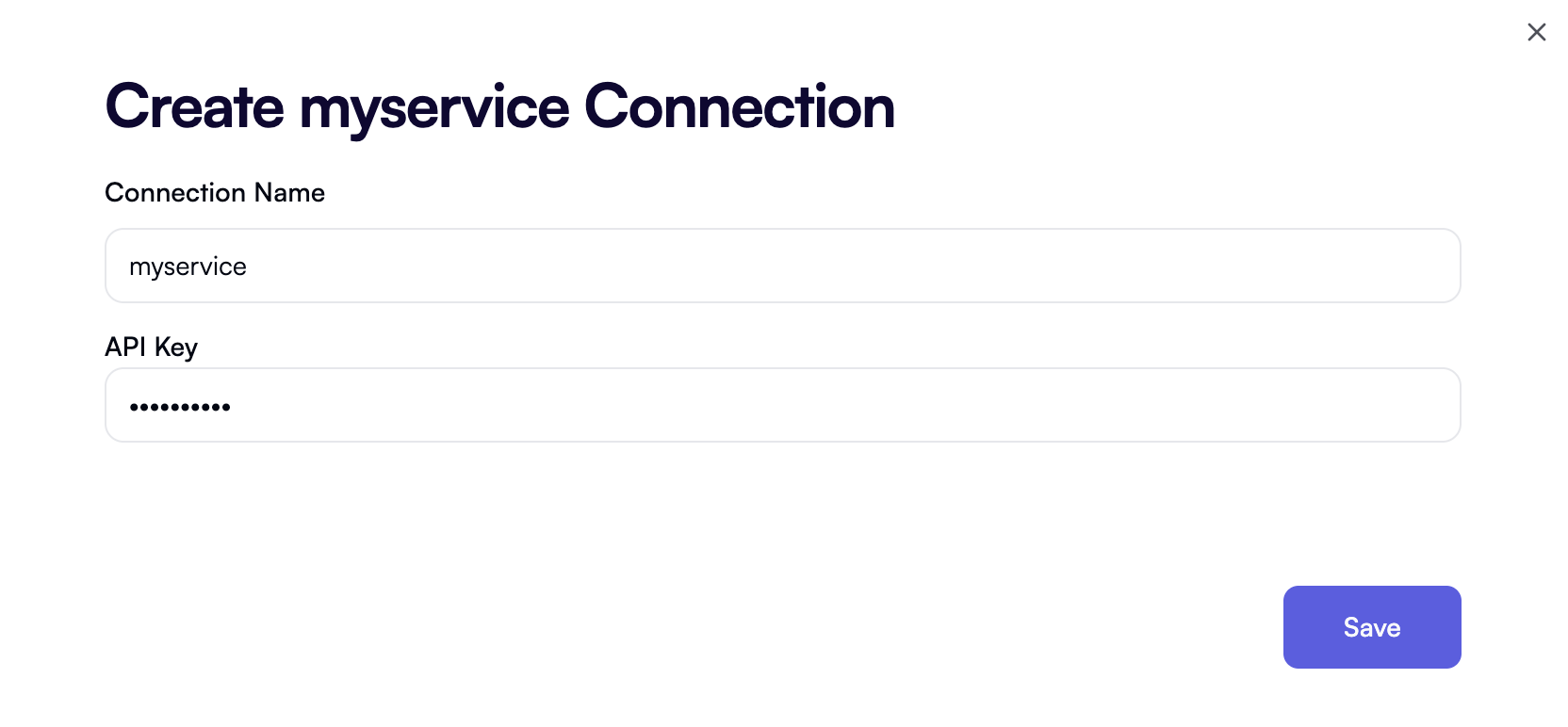
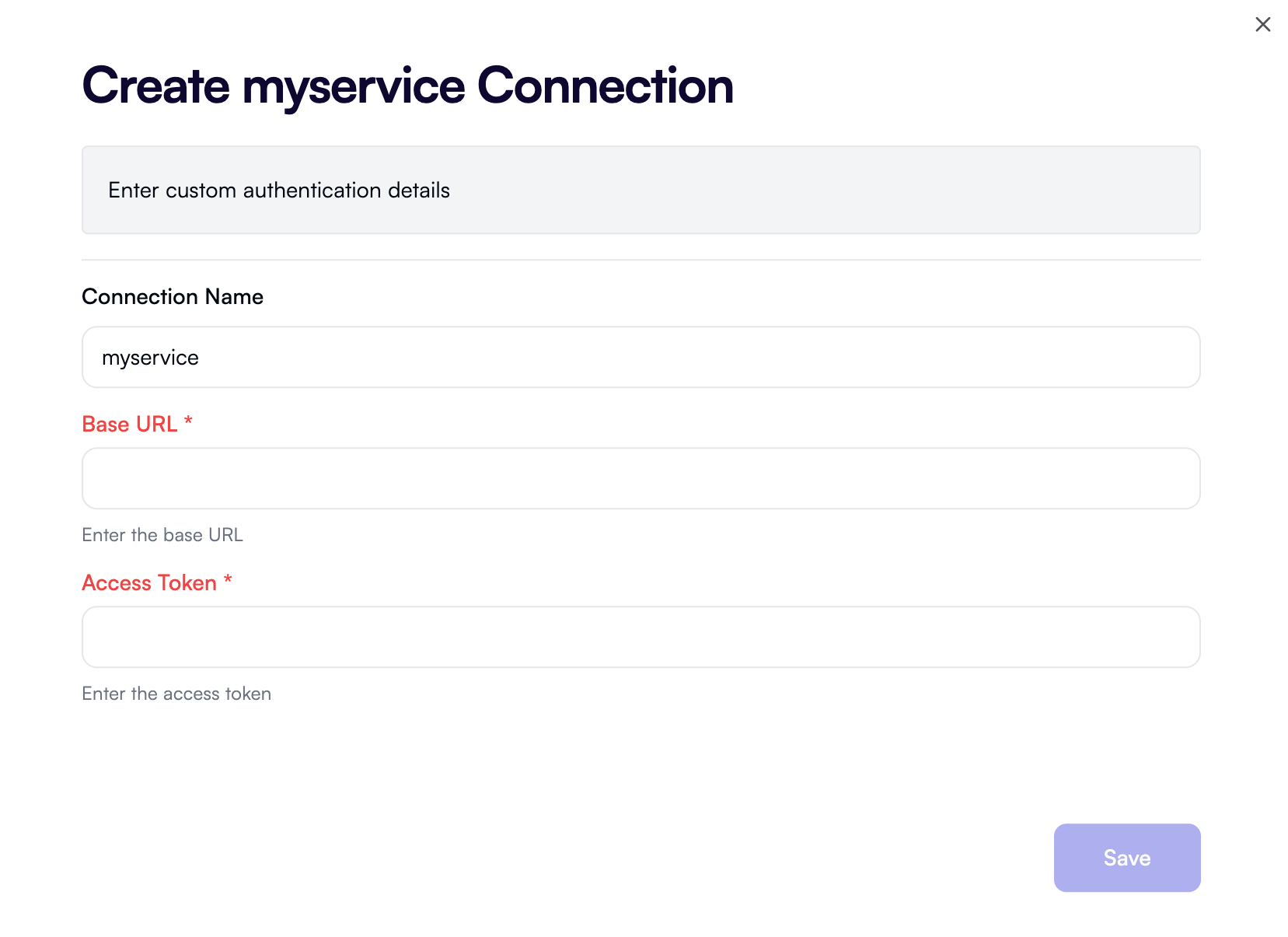
Custom authentication
This type of authentication allows collecting multiple properties, such as a base URL and an access token. Use this type when you need the user to enter more than just an API key. In OpenOps, this is currently the most commonly used authentication type. It’s used by blocks such as AWS, Azure, Google Cloud, Zendesk, Ternary, ServiceNow, Kion, Flexera One, Databricks, and CloudFix. Using the custom authentication type is demonstrated in Contributing an Integration, a guide that explains how to create a fully functional integration block.props object:
OAuth2
This authentication type allows logging in with an OAuth2 provider either on behalf of a specific user (authorization code grant) or on behalf of a service (client credentials grant). It’s currently used by some OpenOps blocks, including GitHub, Slack, Microsoft Teams, and Microsoft Outlook.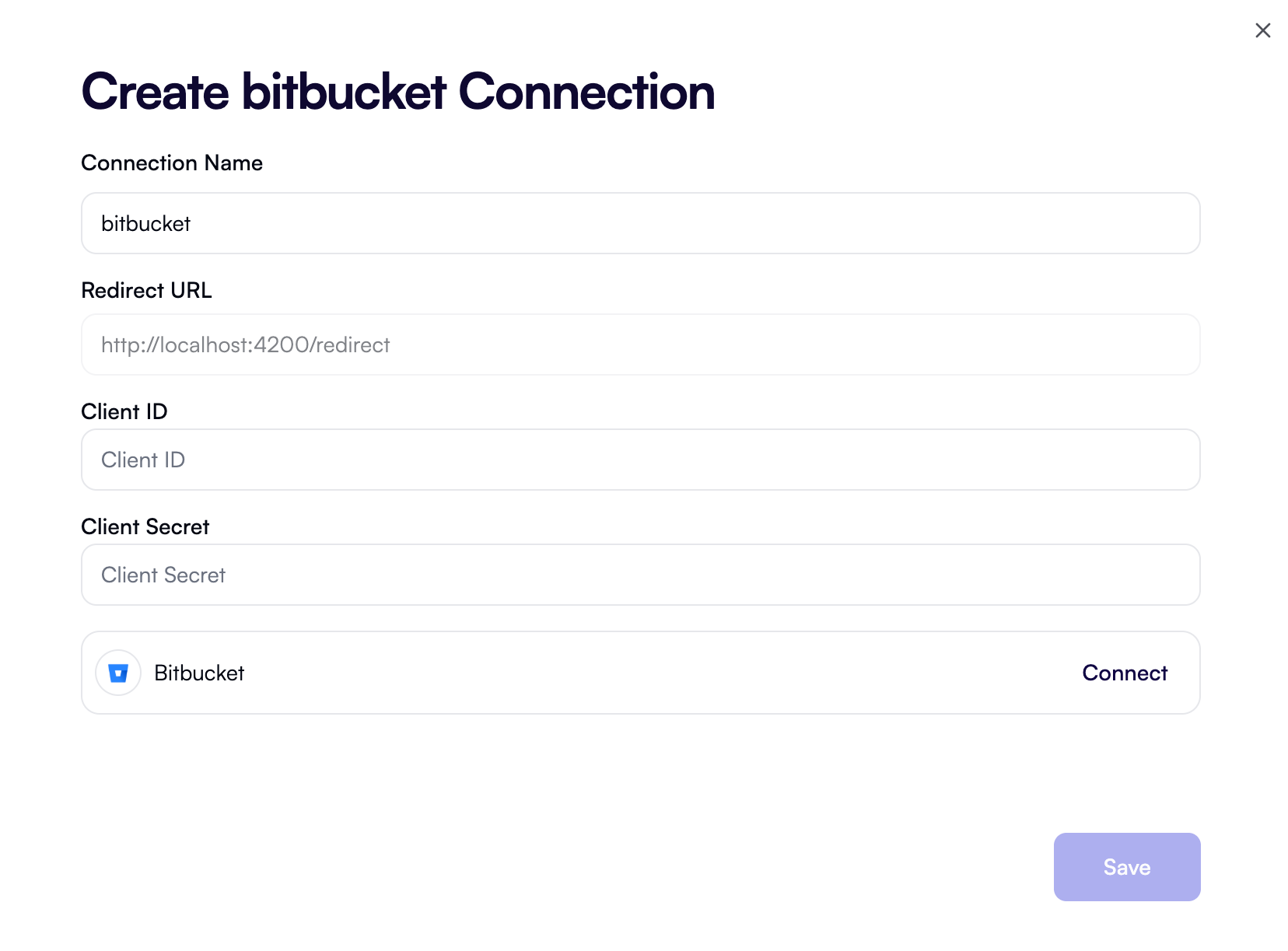
No authentication
If your block doesn’t require authentication, declare this explicitly by assigningBlockAuth.None() to the auth property.